Secure Landing Zone
Enterprise-grade AWS infrastructure. Security, compliance, and governance from day one. Go live in weeks, not months.
Security Guardrails
Eliminate security debt. Automated SCPs and Config Rules protect every account from day one with GuardDuty, Security Hub, and centralized logging.
Multi-Account Strategy
Scale without chaos. Segregation of duties by design across Audit, Log Archive, Shared Services, and Workload accounts.
Hybrid Connectivity
Connect with confidence. Pre-provisioned Transit Gateway and VPN/Direct Connect for seamless on-premise integration.
Audit Ready
Pass audits effortlessly. Mapped to BNM RMiT, PCI-DSS, and ISO 27001 with instant compliance reporting.
Rapid Provisioning
Empower your teams. Account Vending Machine provisions compliant accounts in minutes, not weeks.
Centralized Networking
Control your data. Managed IPAM and centralized egress filtering prevent unauthorized data movement.
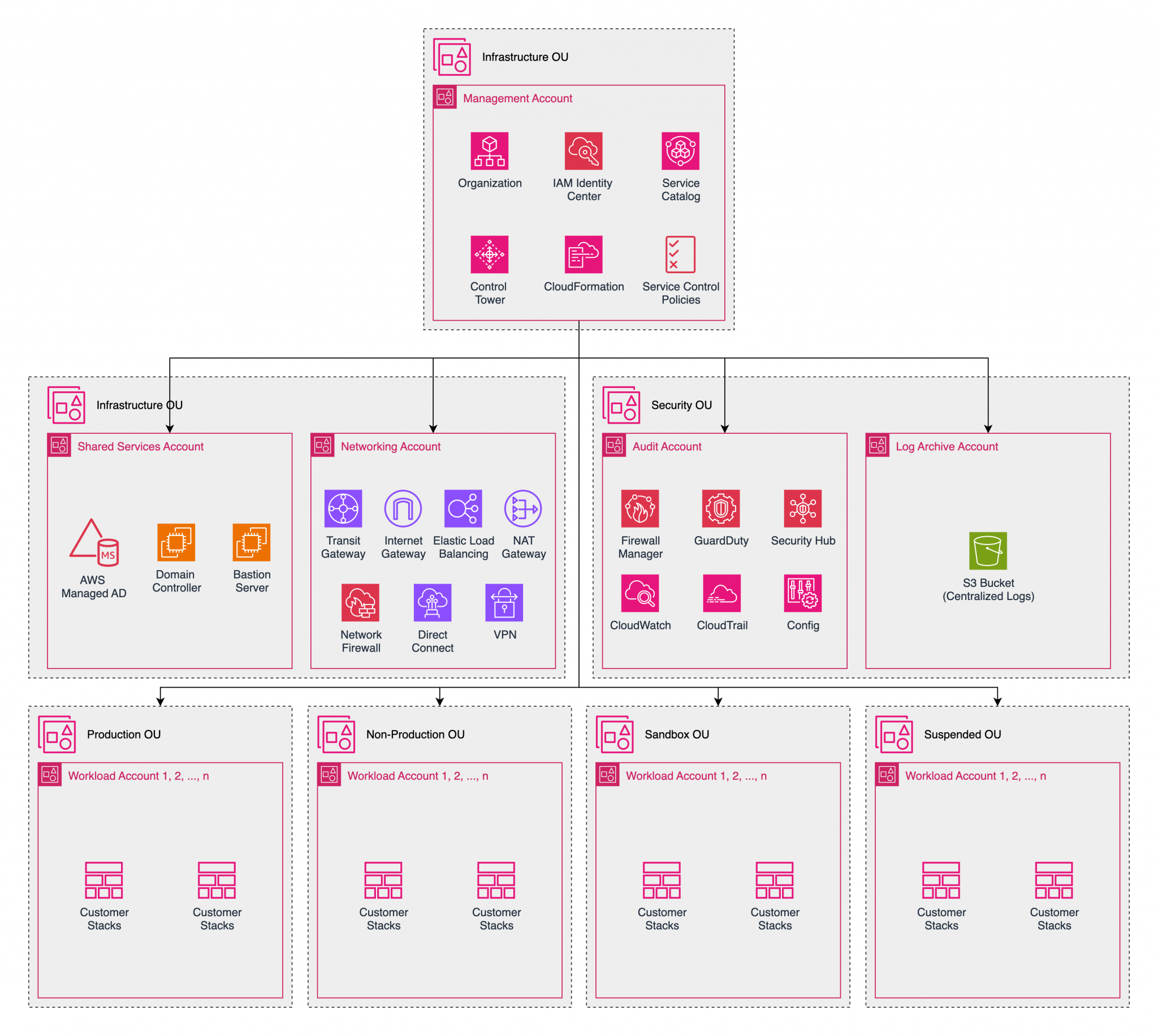
Built for Scale & Compliance
Our AWS Well-Architected reference design decouples management from workloads, giving you operational excellence without the operational burden.
- Core OU: AWS Organization, SCPs, IAM Identity Center, and foundational governance policies.
- Infrastructure OU: Centralized networking, Transit Gateway, and shared services for unified control.
- Security OU: Centralized security tools, monitoring, and compliance enforcement across all accounts.
- Workload OU: Isolated Dev, Staging, and Prod environments with built-in blast radius containment.
From Vision to Production
A proven 5-step delivery model that gets you live faster, with zero surprises.
1. Discover
We listen to your goals
2. Architect
We design your blueprint
3. Implement
We build your foundation
4. Validate
We verify everything works
5. Handover
We empower your team
Advanced Network Security
AWS Network Firewall deployment models for your landing zone
Centralized Model
Single Network Firewall in Shared Services OU. Inspects all north-south (internet) and east-west (inter-VPC) traffic through Transit Gateway. Unified policy enforcement and cost optimization.
Distributed Model
Network Firewalls in each workload VPC. Granular control per environment with lower latency. Best for north-south traffic inspection at VPC boundaries.
Hybrid Model
Centralized for east-west (inter-VPC) via Transit Gateway. Distributed for north-south (internet egress) per VPC. Balances compliance, performance, and cost.
Traffic Flow Patterns
North-South Traffic
Internet-bound and inbound traffic from external sources. Requires inspection at NAT Gateway or Internet Gateway boundaries for threat detection and data exfiltration prevention.
- • Outbound: Workload → Internet
- • Inbound: Internet → ALB/NLB
- • On-premise: Hybrid connectivity via VPN/Direct Connect
East-West Traffic
Inter-VPC and inter-account communication through Transit Gateway. Critical for detecting lateral movement and enforcing zero-trust network segmentation.
- • VPC-to-VPC: Workload ↔ Shared Services
- • Account-to-Account: Cross-account resources
- • Segmentation: Dev ↔ Prod isolation
Hybrid Traffic (Combined)
Optimized inspection strategy combining both north-south and east-west patterns. Centralized inspection for inter-VPC traffic, distributed for internet egress.
- • Central: TGW ↔ Inspection VPC
- • Distributed: VPC → NAT → Internet
- • Balanced: Performance + Compliance
| Capability | Distributed | Centralized | Hybrid |
|---|---|---|---|
| East-West (VPC-to-VPC) | ✗ | ✓ | ✓ |
| North-South (VPC-to-Internet) | ✓ | ✓ | ✓ |
| North-South (VPC-to-On-Prem) | ✗ | ✓ | ✓ |
| Centralized Management | Firewall Manager | Single Instance | Firewall Manager |
| Misconfiguration Risk | Lowest | Medium | Low |
| Cost Model | Per Endpoint | TGW + Endpoint | TGW + Multi-Endpoint |
Ready to Build Your Secure Cloud Foundation?
Let's discuss how we can accelerate your cloud journey while keeping security and compliance at the core.
Schedule a Consultation